Merkle Hash Tree Explained and Its Role in Crypto


Distributed systems like blockchains efficiently and securely verify large volumes of data, which can sometimes feel like trying to find a needle in a haystack. Thankfully, Merkle hash trees come to the rescue and make the process faster and tamper-resistant.
Getting to Grips with the Basics of a Merkle Hash Tree
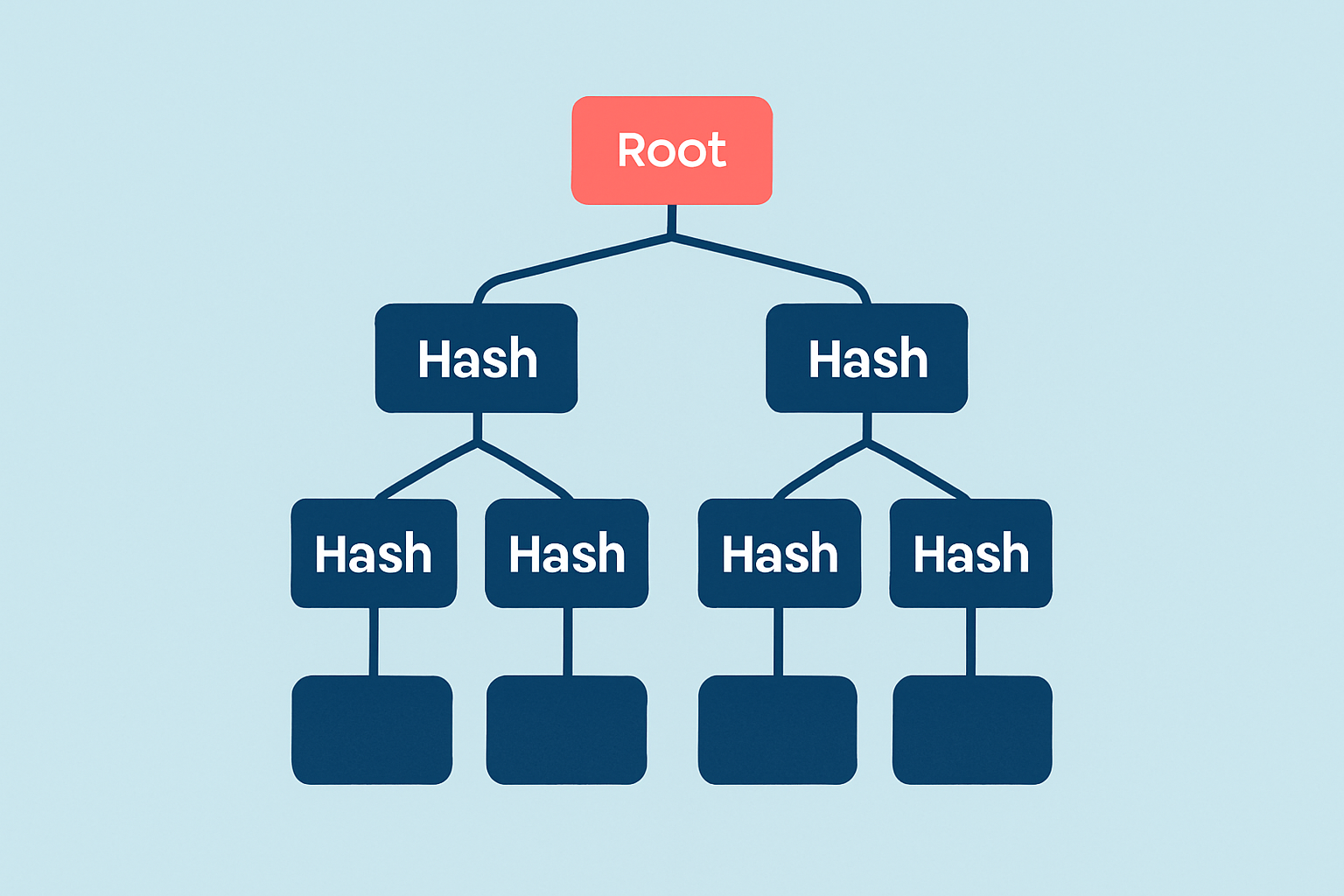
A Merkle hash tree is a clever type of binary tree in computing where each leaf stores a data hash and every parent node holds the hash of its two child nodes.
- Leaf nodes: These are the hashes of the individual data blocks or transactions—the tiniest bits that start it all.
- Intermediate nodes: These are the hashes you get when you combine the hashes from their child nodes like puzzle pieces.
- Root hash: This is the big kahuna, the single hash at the very top representing the integrity of the entire data set.
- Cryptographic hash functions: Secure algorithms that take data and produce fixed-size strings to hash the nodes—like a digital fingerprint but more mathematical.
Imagine a filing system in a bustling office. Each document or leaf node carries its own unique code called a hash. These codes get grouped and summarized into parent hashes like gathering puzzle pieces into a bigger picture. This sorting and summarizing continues up the chain until you reach a single main code known as the root. It stands for the entire pile of files. Rather than sifting through every document, you can check these summary codes.
Getting to Grips with How a Merkle Hash Tree Works, Step by Step
Merkle trees start by hashing each bit of data on its own. Next, these hashes get paired up and mashed together with another hash to build higher-level nodes.
Hash each piece of data to create the leaf nodes—think of it as laying the groundwork.
Take those leaf hashes and pair them up like puzzle pieces coming together.
Hash these pairs to build the next level of parent nodes—this step starts to bring structure.
Repeat the pairing and hashing until you have one final hash.
That last hash, called the root hash, represents the integrity of the entire dataset and holds everything together like glue.
Merkle trees lean on cryptographic hash functions like SHA-256 which produce a unique fixed-length output regardless of the input. A tiny tweak in the input changes the hash completely making any tampering stand out like a sore thumb.
The Importance of Merkle Hash Trees in Blockchain
When it comes to blockchain, Merkle hash trees are like the unsung heroes working quietly behind the scenes. They might not grab headlines, but they play a vital role in keeping everything honest and efficient. Think of them as the ultimate proofreaders, double-checking the data with a kind of digital fingerprint that’s both clever and trustworthy. Without these neat structures, the whole system would be a lot clunkier, slower, and, frankly, less secure. In my experience, understanding Merkle hash trees really feels like unlocking a secret level of how blockchain manages to keep everything so airtight while still moving at lightning speed.
In the world of blockchain, Merkle trees are like the unsung heroes that help users verify transactions inside blocks without breaking a sweat. Instead of downloading the entire blockchain, users get to quickly and securely check specific transactions just by looking at the root hash.
- Merkle trees play a key role in making sure all transaction data remains intact and untampered with while keeping things on the up and up.
- They give lightweight clients a clever way to verify transactions without the headache of downloading entire bulky blocks.
- They offer speedy and efficient proofs known as Merkle proofs that clearly show data is included, kind of like a digital receipts book.
- By trimming down the amount of data that needs handling, they boost both blockchain scalability and security, killing two birds with one stone.
Traditional verification means downloading and checking every single transaction, which can quickly turn into a slow and clunky process. Merkle trees are a nifty solution that lets users verify the presence of a specific transaction by relying on just a handful of hashes, rather than digging through the entire block data.
Imagine a Merkle tree like a library catalog index that’s cleverly designed to save you tons of time. Instead of rifling through every single book on the shelf (which, let’s face it, can be a real headache), you simply look up its unique code in the catalog. That way, you can quickly and confidently confirm the book’s presence without breaking a sweat.
Real-World Applications of Merkle Hash Trees Beyond Blockchain—A Closer Look
Merkle trees are a staple in the blockchain world but their usefulness stretches far beyond that. For instance, distributed file systems like IPFS use them to keep file integrity in check—a trusty watchdog for your data. Databases also turn to Merkle trees to ensure everything stays in sync securely while quietly doing the heavy lifting behind the scenes.
- They help keep data humming along smoothly across distributed systems, doing so in a way that is both secure and pretty efficient.
- Merkle proofs come in handy for quickly confirming that a particular piece of data belongs in a dataset, no fuss attached.
- They’re the go-to when you want to verify file contents without the headache of transferring the entire file, which is a real lifesaver for saving bandwidth.
- They play nice with incremental updates by checking just the changes, so you’re not stuck reprocessing the whole dataset every single time.
Common Misunderstandings About Merkle Hash Trees That Trip People Up
Merkle trees tend to trip up people who are new to the concept and often lead to some classic mix-ups. For instance, people might assume they’re overly complicated or solely tied to cryptocurrencies. Some also think they magically provide privacy on their own.
- Merkle trees are not about encrypting data or keeping user info under lock and key. Their main purpose is to double-check that data hasn’t been tampered with.
- You’ll find them popping up in many technologies beyond cryptocurrency.
- Instead of storing the actual data or transactions, Merkle trees hold hashes, which are like digital fingerprints.
- They speed up verification but don’t fully solve all the scalability headaches that blockchains face.
How Developers Actually Use Merkle Hash Trees in Cryptocurrency Projects (And Why It Matters More Than You Think)
Blockchain developers often lean on Merkle trees inside smart contracts and protocol design to pull off things like transaction verification and keeping cross-chain communication smooth.
- Building block headers that pack the root hash to speed up verification, cutting down the wait time nicely.
- Letting Simplified Payment Verification (SPV) clients confirm transactions with just the bare minimum of data.
- Handling state proofs that peek at blockchain states without spilling all the details, keeping things tidy and secure.
- Supporting light nodes that lean on Merkle proofs to securely link up with the network, making sure everything stays connected without the heavy lifting.
When you’re checking whether a transaction is included, a Merkle proof hands you just the branch of hashes needed to link that transaction back to the root. It’s a neat little package compact and speedy to verify.
Conclusion on How Merkle Hash Trees Keep Leaving Their Mark on Crypto
Merkle hash trees are essential for building trust and security in decentralized systems. They play a big role in making blockchains scalable and efficient—a bit like unsung heroes working quietly behind the scenes. As crypto technologies evolve rapidly, these trees hold their ground by enabling faster and more secure ways to verify data.






