Symmetric Encryption vs Public Key Cryptography


Understanding encryption has become pretty key for anyone who gives a hoot about online security nowadays. This article takes a friendly stroll through the main differences between symmetric encryption and public key cryptography—two fundamental techniques that do the heavy lifting to keep your data under lock and key.
Encryption might sound like a tough nut to crack but at its heart, it’s really just about turning readable data into a secret code to keep prying eyes at bay. It’s what helps safeguard sensitive info—think passwords or credit card details—whether it’s zipping across the internet or sitting quietly in storage. Kick things off by diving into symmetric encryption, one of the oldest yet still pretty popular methods.
What Exactly Does Symmetric Encryption Mean Anyway?
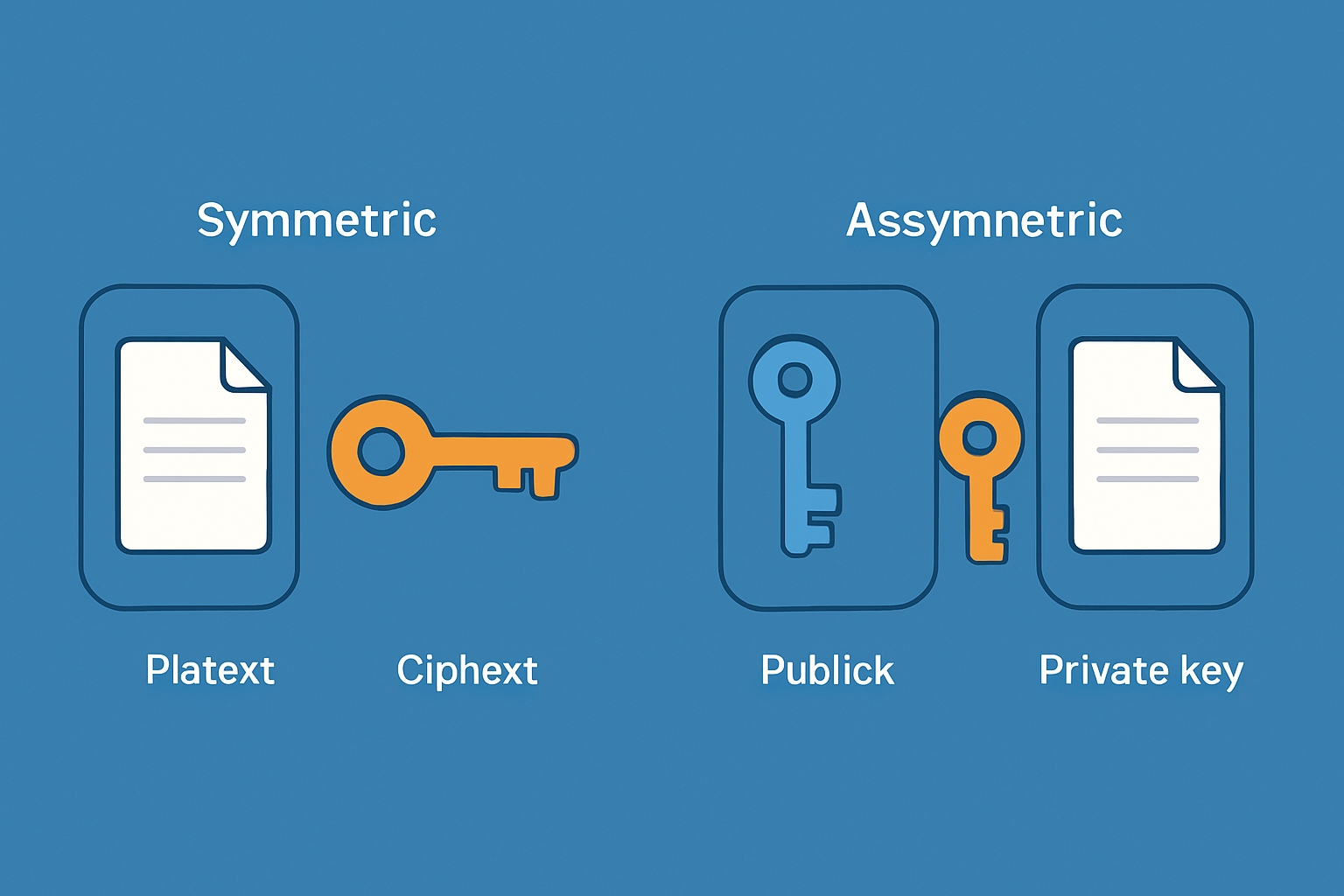
Symmetric encryption leans on a single secret key that both the sender and receiver use to lock up (encrypt) and unlock (decrypt) messages. Picture it like sharing one key to a treasure chest that only you and a trusted friend hold onto. Keeping this key under wraps is absolutely vital—otherwise, someone else might sneak in and rummage through what’s inside.
- Symmetric encryption relies on a single shared secret key for both locking and unlocking your data—keeping things straightforward.
- It’s celebrated for being quick and efficient which makes it a go-to when dealing with hefty amounts of data that need securing without slowing everything down.
- Some crowd favorites in the symmetric world are AES (Advanced Encryption Standard) and DES (Data Encryption Standard)—tools you’ve likely heard of.
- You’ll spot symmetric encryption in disk encryption, VPN tunnels, and safeguarding files or databases where speed is the name of the game.
What on Earth Does Public Key Cryptography Actually Mean?
Public key cryptography, often called asymmetric encryption, is built around a clever pair of mathematically linked keys. One is public and one is private. The public key is shared openly and used to lock information while the private key stays secret, unlocking data only for those in the know.
- Public key cryptography relies on a pair of keys: one public key to lock things up (encrypt) and a private key to unlock them (decrypt).
- Since it’s asymmetric these keys aren’t interchangeable. This setup lets people share secrets securely without planning or exchanging keys beforehand.
- Some go-to algorithms in this arena include RSA and ECC (Elliptic Curve Cryptography). They’re the popular kids on the block.
- You’ll find this kind of magic behind the scenes securing web traffic (think SSL/TLS), signing digital documents and scrambling emails to keep prying eyes at bay.
Taking a Closer Look at Symmetric Encryption and Public Key Cryptography
Both encryption methods play a vital role, yet they come with their own quirks. Symmetric encryption is generally quicker and more efficient, though it hinges on the not-so-trivial task of safely sharing the key. Public key cryptography shines when it comes to secure key exchange and digital signatures, but it tends to be a bit slower and can be a real headache on computing resources.
| Feature | Symmetric Encryption | Public Key Cryptography |
|---|---|---|
| Key Type | Uses a single secret key, kind of like having one key to rule them all | Involves a dynamic duo: one public key you can shout from the rooftops, and a private one you keep under lock and key |
| Speed | Generally lightning fast and efficient, especially when handling large chunks of data | Usually a bit slower thanks to the heavy-duty math behind the scenes, so patience is a virtue here |
| Security Level | Packs a solid security punch but depends heavily on carefully keeping that secret key under wraps | Offers top-notch security and backs it up with safe key exchanges and trusty digital signatures, making it a strong contender |
| Key Distribution | You’ve got to be crafty about sharing the secret key securely, or you’re in trouble | The public key goes out for a stroll in the park freely, while the private key stays tucked away safely |
| Example Algorithms | AES, DES, 3DES, the classic lineup | RSA, ECC, DSA, your go-to heavy hitters for public key cryptography |
The table lays out clearly why symmetric encryption usually steals the spotlight when speed matters—think encrypting files or streaming data without breaking a sweat. That said, it does come with a catch: you have to have a secure way to share keys ahead of time, which can be a headache. On the flip side, public key cryptography is not winning any races in speed but sidesteps this problem by letting you exchange keys and authenticate securely without needing a shared secret first.
How Symmetric and Public Key Encryption Work Together Like an Unlikely but Effective Duo
Symmetric and public key encryption team up within hybrid systems to play to each of their strengths. For example, when you hop onto a secure website, public key cryptography steps in to securely share a symmetric session key. Then that session key takes over and handles the faster encryption of the data itself.
- The sender wraps up a symmetric session key with the receiver’s public key and keeps it under lock and key.
- This cleverly encrypted session key takes a secure trip across the network without detours.
- On both ends the session key works its magic and quickly encrypts and decrypts the main data like a well-oiled machine.
- Once the session wraps up the symmetric key is tossed aside to keep communication temporary and secure.
Picture hybrid encryption like a trusty courier service you’ve come to rely on. It kicks off with a locked mailbox (public key cryptography) to swap the key safely, then zips along with the heavy lifting—delivering big packages in a flash using speedy symmetric encryption.
Common Misconceptions That Often Trip People Up About Symmetric and Public Key Encryption
There are quite a few myths swirling around these types of encryption that can easily trip up anyone new to the topic. Some people think symmetric encryption is old-fashioned or downright insecure, while others assume public key cryptography is always too slow to be practical.
- Symmetric encryption isn’t some insecure relic when the keys are handled with care. It actually provides pretty robust protection.
- Public key cryptography isn’t necessarily the slowpoke everyone imagines. Thanks to ongoing improvements and better hardware, the lag has been reduced quite a bit.
- The keys in symmetric and asymmetric setups aren’t exactly interchangeable because each one has its own unique job to do.
- Encryption definitely boosts privacy but doesn’t guarantee total privacy, especially if those keys or devices fall into the wrong hands.
Real-World Applications and Use Cases That Actually Matter
Encryption technologies are the unsung heroes quietly protecting our day-to-day digital lives. When speed really matters—think encrypting files or zipping through VPN traffic—symmetric encryption usually takes the lead. On the flip side, public key cryptography backs up the scenes with SSL certificates that keep websites locked down tight and digital signatures that give us peace of mind about data integrity.
- Symmetric encryption is a go-to method for keeping files and disks locked up tight, making sure stored data stays under wraps.
- VPN services lean heavily on symmetric encryption to craft those secure tunnels that keep your internet traffic out of prying eyes.
- Full disk encryption on laptops uses symmetric algorithms as trusty bodyguards against data theft.
- Public key cryptography secures web sessions with SSL/TLS certificates, adding a key layer of trust.
- It is the secret sauce behind email signing and encryption, helping to confirm who is sending what while keeping things private.
- Cryptocurrency wallets rely on asymmetric keys to manage and sign transactions with solid security, ensuring your digital coins stay safe and sound.
Symmetric encryption usually runs lightning fast and is perfect for handling large chunks of data in a flash—think streaming or disk encryption scenarios. On the flip side, public key cryptography plays the key role of building trust. It’s all about verifying identities and securely swapping keys, forming the backbone of secure internet communication.
What’s Shaping the Future
Emerging technologies like quantum computing are shaking things up, bringing a mix of fresh challenges and exciting opportunities for encryption methods. Quantum algorithms have the knack for cracking some public key systems by taking on problems we once thought were tough nuts to crack.
Organizations like NIST are constantly digging deeper and pushing forward to standardize new encryption algorithms that can withstand the looming threat of quantum attacks. These efforts focus on clever approaches such as lattice-based and code-based cryptographic methods as well as multivariate techniques, each with its own quirks and promise. Meanwhile, symmetric encryption algorithms are not being left out or forgotten. They are under close watch as experts work to increase key sizes and keep their security strong.






